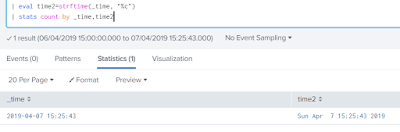
Directory structure of Splunk
Splunk Home: /opt/splunk Path where Splunk resides. Binaries: $SPLUNK_HOME/bin All binary executables are present here. Config: $SPLUNK_HOME/etc Most important directory of Splunk, it contains everything related to configuration files, installed apps, etc. Logs: $SPLUNK_HOME/var logs/splunk: All the logs of Splunk applications are stored. lib/splunk: Default DB location, where all parsed data along with metadata information is stored. PS: Contains other directories as well but the mentioned above, are quite important.